Background
Modern mobile communication faces multiple security challenges, including man-in-the-middle attacks, fake base station interception, and vulnerabilities in signaling systems at the network level. At the device level, risks arise from malicious apps and system flaws. Excessive data collection by apps and cloud synchronization further increase privacy risks. Inadequate or bypassed encryption mechanisms make communications more susceptible to eavesdropping or tampering. Additionally, phishing messages and social engineering have become significant human-related threats to information security.
Secure Communication Requirements
The main requirements for secure mobile communication are:
- Ensuring voice calls are encrypted to prevent eavesdropping and decryption of normal communication content.
- Encrypting the sending and receiving of text messages to avoid interception.
- Having an independent, encrypted secure space on the phone to protect sensitive content in case the device is lost or the password is compromised.
Solution

MTESS( mobile trusted environment sense system )
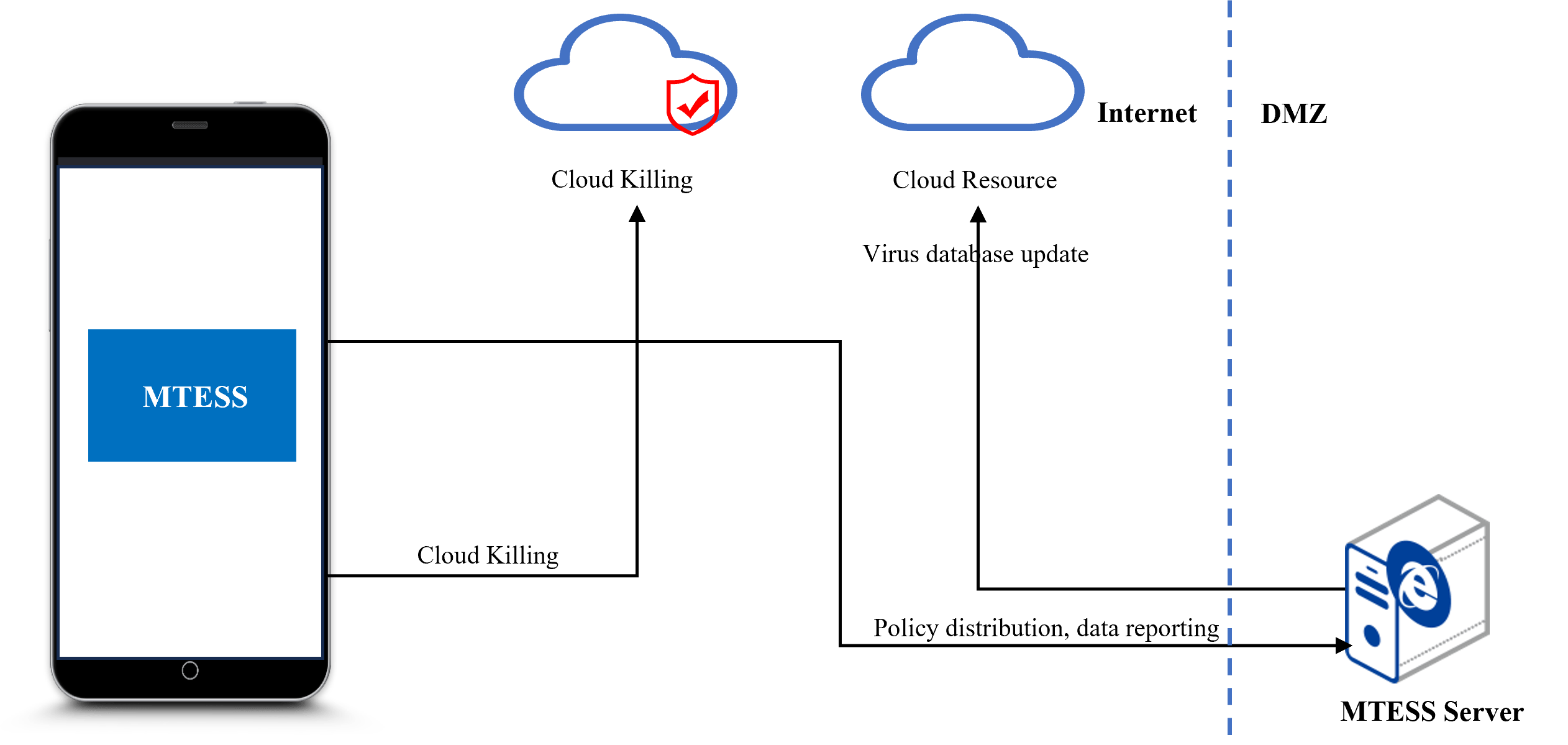
Perceived risk visualization
The context-aware platform supports the display and statistics of the risk-aware data in the current system.
Flexible deployment
It can be integrated with enterprise business applications, and can also be deployed as an independent app.
Total information awareness
Risk perception and reporting will be triggered by changes in mobile terminals and sensitive behaviors.
Smarter evaluation rules
The device risk scoring rules set based on environment-aware big data are more reasonable and in line with mobile security scenarios.
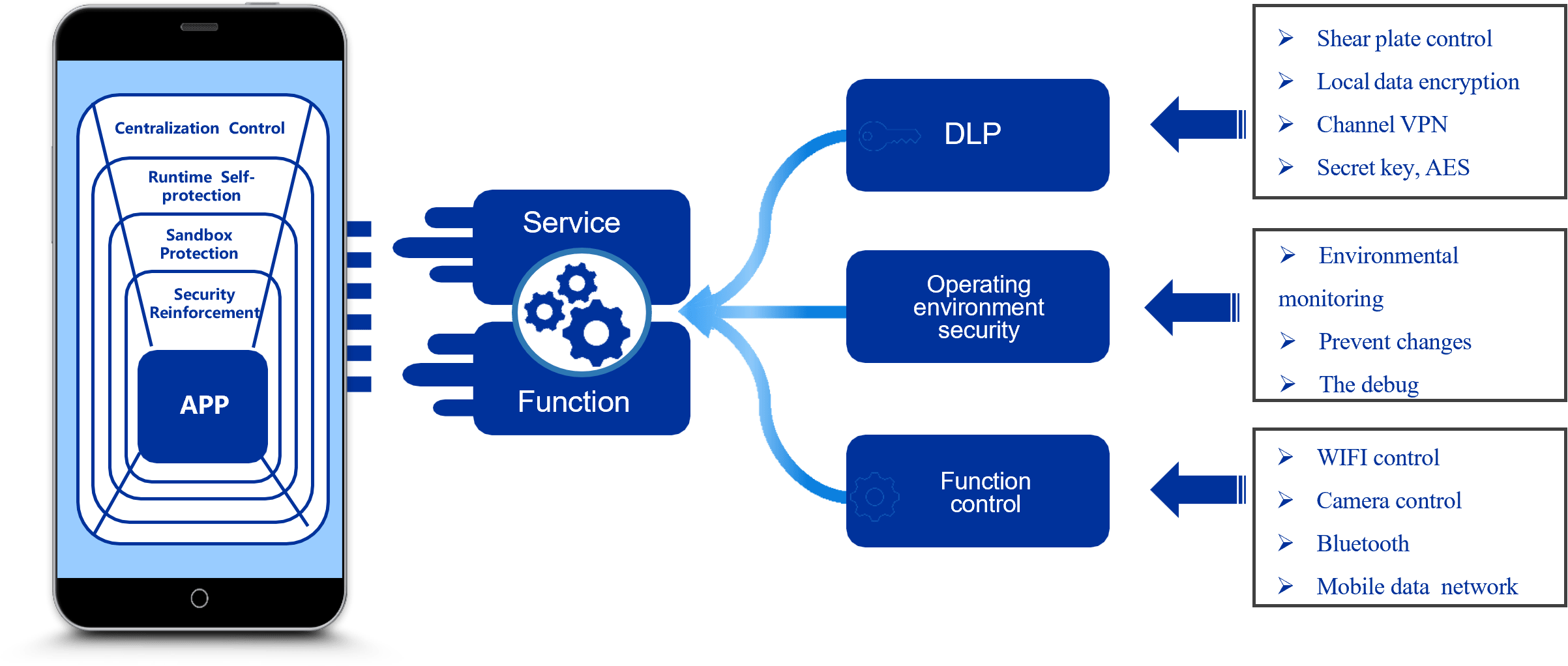
MIAP (Mobile In-app protection And Security)
Through the aggregation of multiple security technologies, many application security protection measures are automatically integrated into the internal of the enterprise app, and the enterprise app self-generated security system is constructed to ensure the application security and data security of the enterprise app.
Trustspace
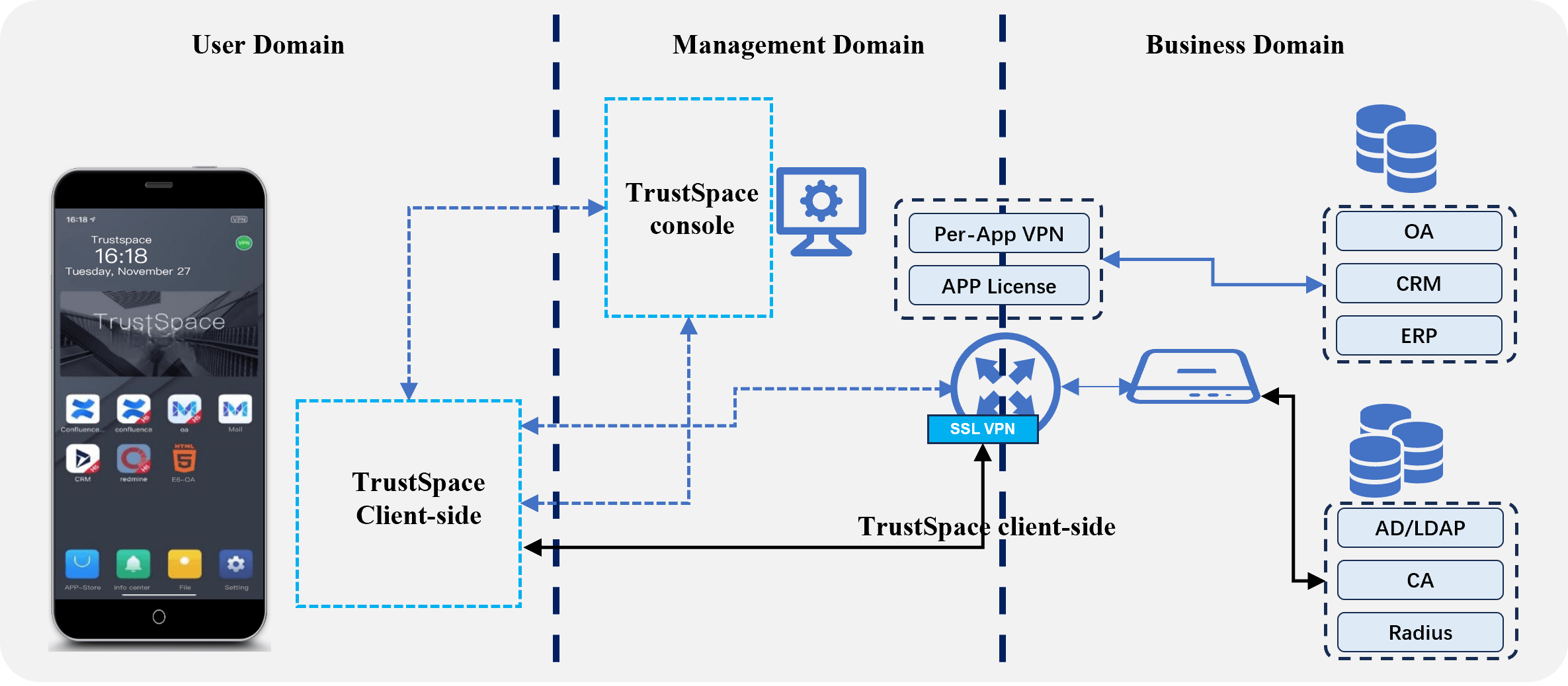
Mobile security management system
- App&key sandbox
- Mobile threat detector
- Data leakage prevention
- Mobile device management
Application gateway
- Tunneling
- Privilege control
- Encryption & decryption)
ID intelligent identity platform
- Multi-factor authentication
- Single-sing on
- Unified user center
Enc-call
- Support 2G/3G cellular network encrypted calls, support 4G VoLTE encrypted calls.
- End-to-end digital voice encryption with ECDH/AES256 cryptographic algorithm.
- Multiple security features such as operating system protection, SMS encryption, data encryption, etc. Dual OS support, Separation of public and private apps&data to enhance security(Option).
Localized Deployment
Localized deployment ensures data and link security.

Solution Advantages
- Compatible with mainstream mobile OS

- Compatible with devices of mainstream mobile manufacturers

- Experience
With years of experiences working in mobile security field, the team is able to provide full range of mobile security solutions to satisfied customers’ requirements.
- Capability
Based on the in-depth study of various mobile OS and mobile devices, the team is able to provide flexible APP, SDK, API adaptation capabilities.


