Background
In the financial services sector, due to the complexity and sensitivity of information involved, the construction of platform data security and personal information protection has become particularly important. The financial industry has successively introduced a number of standards related to personal financial information and data security. In response, financial institutions and service platforms have increasingly prioritized and invested in the protection of personal information and data security.
Typical Data Security Requirements in the Financial Industry
Solution
Centered on a Data Security Situational Awareness Platform, the solution achieves comprehensive monitoring of network communication traffic by deploying a data security traffic monitoring system. At the same time, it integrates endpoint data leakage prevention capabilities—including both endpoint and network DLP—creating a holistic “endpoint + network” data security operational framework, with “people and data” as its core.
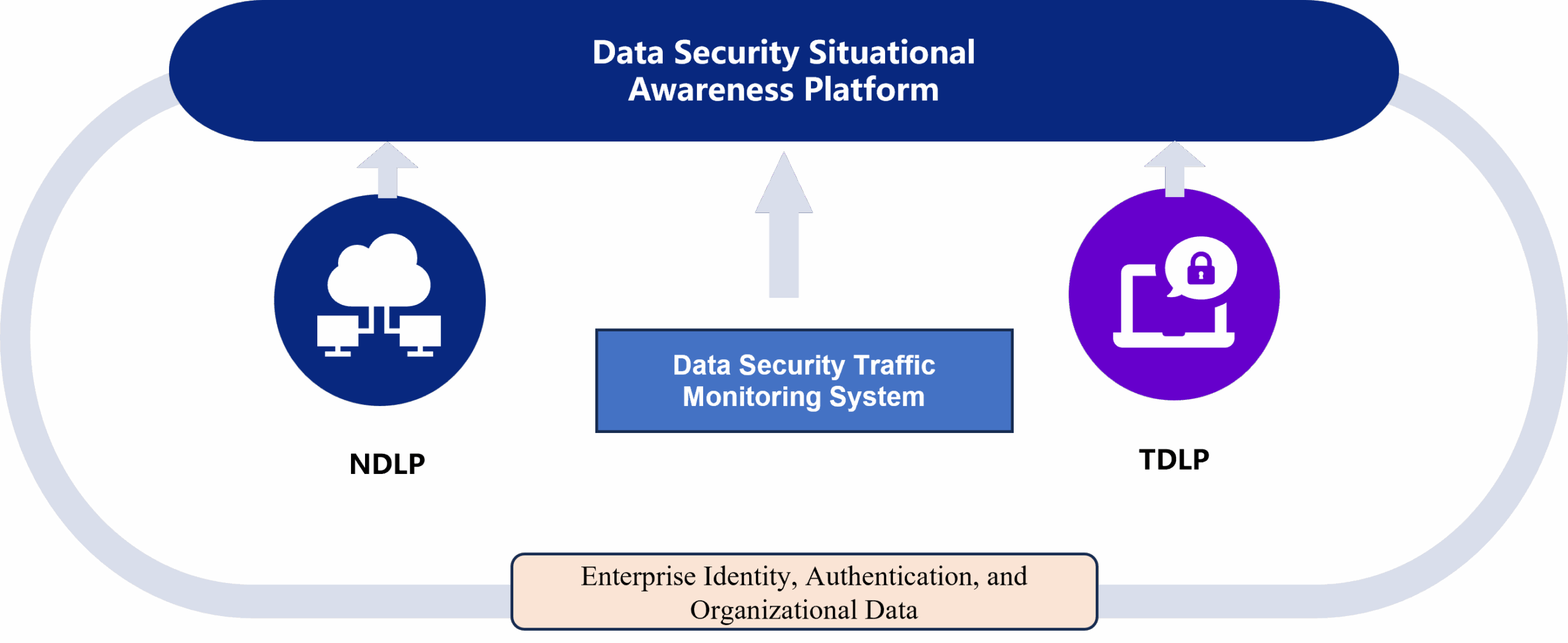
Data Security Traffic Monitoring System
The Data Security Traffic Monitoring System is designed to detect and analyze data security risks based on network communication traffic. With strong capabilities in traffic feature analysis, protocol reconstruction, content parsing, and behavior analysis, the system can monitor and detect violations and illegal behaviors related to data security in real time through built-in alert rules. This enables visualized supervision of data security incidents and facilitates detection and early warning of risks from the “network side.”
Data Leakage Prevention (DLP) Capabilities
By deploying and integrating endpoint DLP , and network DLP systems, the solution achieves full-scale monitoring and effective blocking of sensitive data. It provides detailed audit data from the endpoint for security risk detection and personnel behavior analysis, building a complete set of auditing and control capabilities for data security on the endpoint side.
Integration of Correlated Data Sources
The platform also integrates data from organizational structures, identity authentication systems, single sign-on (SSO) systems, IT assets, and other data security-related sources. These are used for correlation analysis and risk mining to enhance overall security posture awareness.
Solution Advantages
Full-Link Data Flow Visibility
Leveraging unique content fingerprinting and multi-dimensional correlation analysis technologies, the solution enables visual presentation of data flow channels and full-path tracking, providing a comprehensive view of the overall data flow landscape.
Comprehensive and High-Precision User Profiling
Utilizing correlation analysis, User and Entity Behavior Analytics (UEBA), and Natural Language Processing (NLP), the solution constructs detailed behavioral and content profiles of users to predict trends in security risks.
Global Mapping of Digital Assets
Performs comprehensive monitoring of sensitive assets within the regulatory scope through a combination of endpoint and network insights, and presents asset distribution visually in alignment with organizational structures.
Multi-Level, In-Depth Response to Data Security Incidents
Takes security events as the starting point and utilizes security orchestration and automation capabilities to quickly coordinate with endpoint systems, network access controls, Single Sign-On (SSO), domain controllers, and other infrastructure. This enables multi-level, in-depth incident response with rapid reaction and effective loss mitigation.Comprehensive Traceability of File Transfers
Offers holistic monitoring and forensic analysis capabilities based on file entities, content fingerprints, and watermarks. This supports deep-level traceability and investigation of data leakage incidents.
Customer Benefits
Visualized, Routine, and Automated Data Security Operations
Through the implementation of this solution, customers can achieve visualized, standardized, and automated data security management, ensuring secure and compliant business operations.
Visual Management of Digital Assets
With the deployment of the system, customers gain a global view of the distribution and flow of current digital assets, enabling more effective asset governance.
Easier Compliance with Industry Regulations
The solution’s closed-loop capabilities in data identification, monitoring, flow tracking, analysis, and response can cover the majority of requirements in data security inspections. It enables early detection and remediation, helping customers easily meet regulatory demands.
Automated Risk Monitoring and Rapid Response
Scenario-based risk detection models can automatically identify violations and high-risk behaviors, allowing for swift response and mitigation. This significantly reduces the impact of data security incidents.