Background
The client is a global leading integrated communication solutions provider with multiple data centers worldwide. The assets within the data centers are increasingly cloud-based, and the business systems hosted on these assets are becoming more microservice-oriented (Dockerized), which is becoming more pronounced. However, the security risks brought about by new technologies are also gradually increasing, presenting significant challenges to the client’s security department.
Among them, the account security management of target assets is one of the most important challenges the client’s security department is currently facing.
Customer Challenges
The user believes that the current issues they face in account security management are mainly as follows:
- The business systems running in Docker have embedded database and associated system usernames and passwords, which leads to users being afraid to modify these passwords and worried about others modifying them.
- The account security management of the operating systems (OS), databases, and middleware that host the business systems mainly relies on traditional bastion hosts. However, this approach has a limited coverage, lacks functionality, and heavily depends on administrators for configuration, making it difficult to prevent account security risks.
Solution
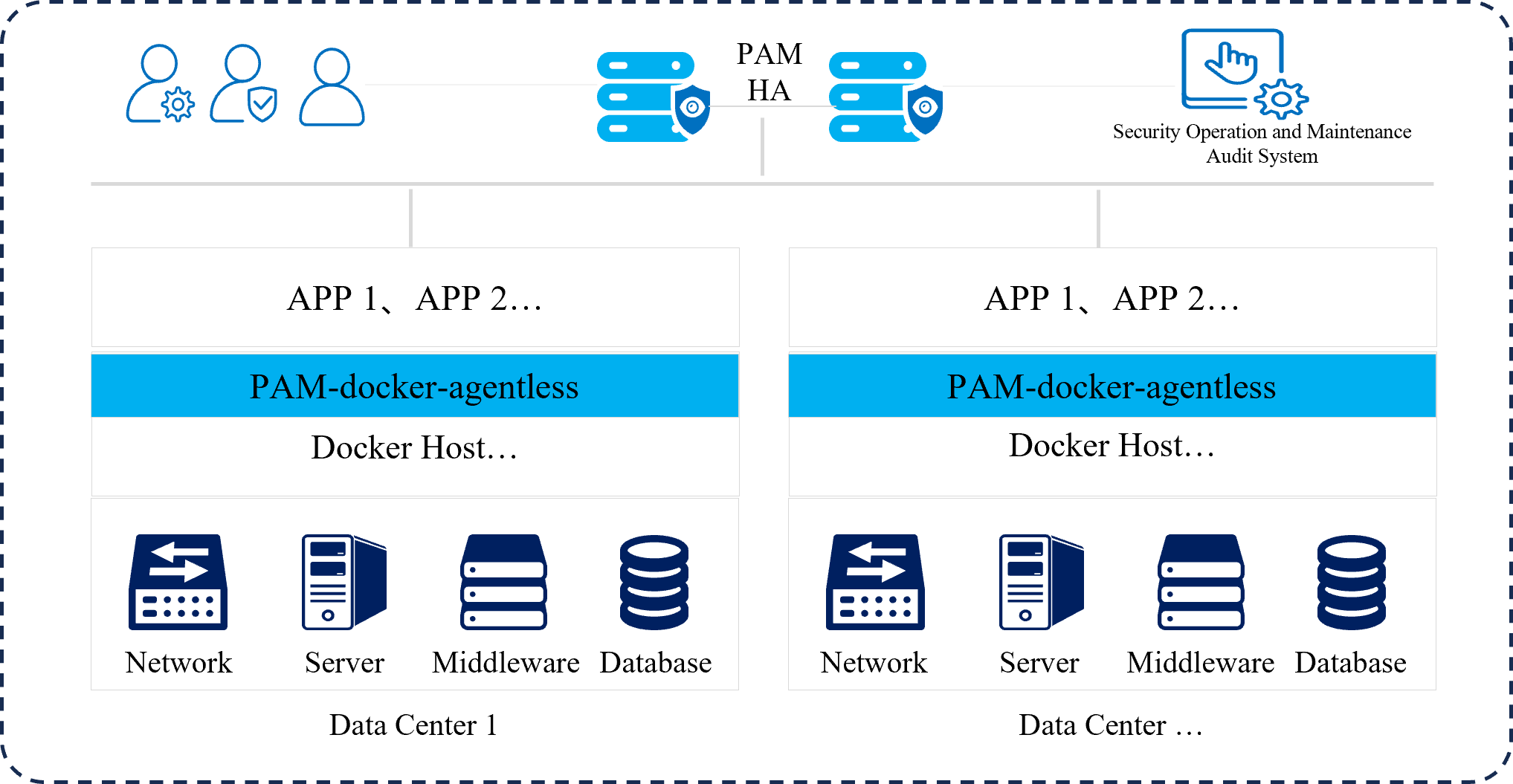
By deploying PAM (Privileged Access Management) in the client’s main data center, the following objectives are achieved:
- Deploying the agentless SDK of PAM in the Docker host, allowing business systems to dynamically and securely call embedded usernames and passwords through the SDK, making the modification of various usernames and passwords feasible.
- Thoroughly organizing and managing the usernames on the foundational assets and the embedded usernames in the business systems. Through intelligent analysis, the system automatically detects abnormal risks in the usernames and provides the necessary channels and data support for further optimization of security management.
Insight into account risks, realizing embedded account security management for Docker applications, and enhancing the user’s security management capabilities.



