Product Overview
Web application isolation and protection is built on state-of-the-art digital phantom technology, providing secure isolation and protection capabilities forenterprise web applications. The system does not require the implantaion of additional security components (or script), ensuringuninterrupted web business continuity and preserving users’ original browsing habits, lt operates independently of rule-basedsystems, significantly reducing the occurence of false positives and missed detections of unknown risks. This empowers enterprise security teams to easily manage the ever-changing landscape of web security risks
Key Features & Functions
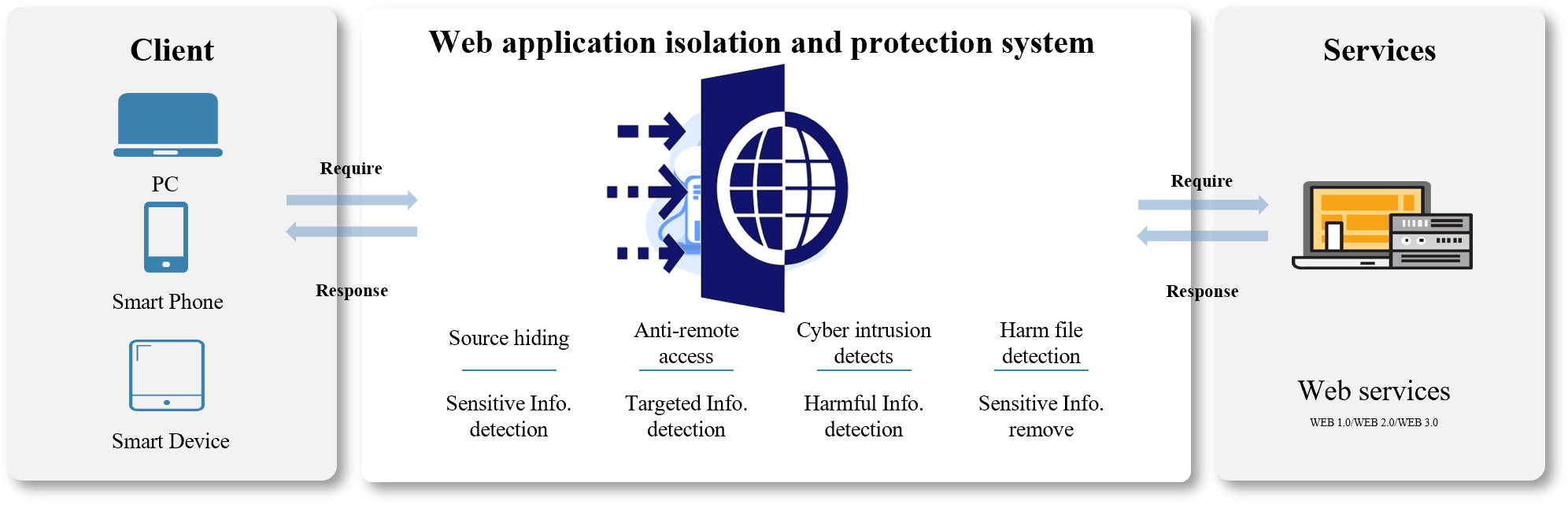
Cybersecurity Protection
Source site address hiding
Hiding the source server lP, attackers can not directly target the source host.
Source site vulnerability concealment
lsolate middleware and web vulnerabilities on the source server, blinding scanning devices.
Source site Apl concealment
lsolate exposed Web APls to prevent exploitation by attack tools/scripts.
Source site Code concealment
The source site’s page code cannot be displayed on the Visitor’s browser.
Source site URL concealment
Prevent attackers from executing specific path web attacks.
Data Protection
Business source code can be concealed
Hide source server informa-tion such as lP and URL.Block interaction of JS,HTML, and other code.
Web crawler access can be managed
Prevent web crawling datacollection. Eliminate therisk of website cloning.
Sensitive data Can bedesensitized
Support dynamic informationcontent desensitization.Covering phone numbers, IDnumbers,lPs, etc.
Access authorization can be controlled
Support website transparenttransmission, silent mode.Support visitor file uploadand download management.
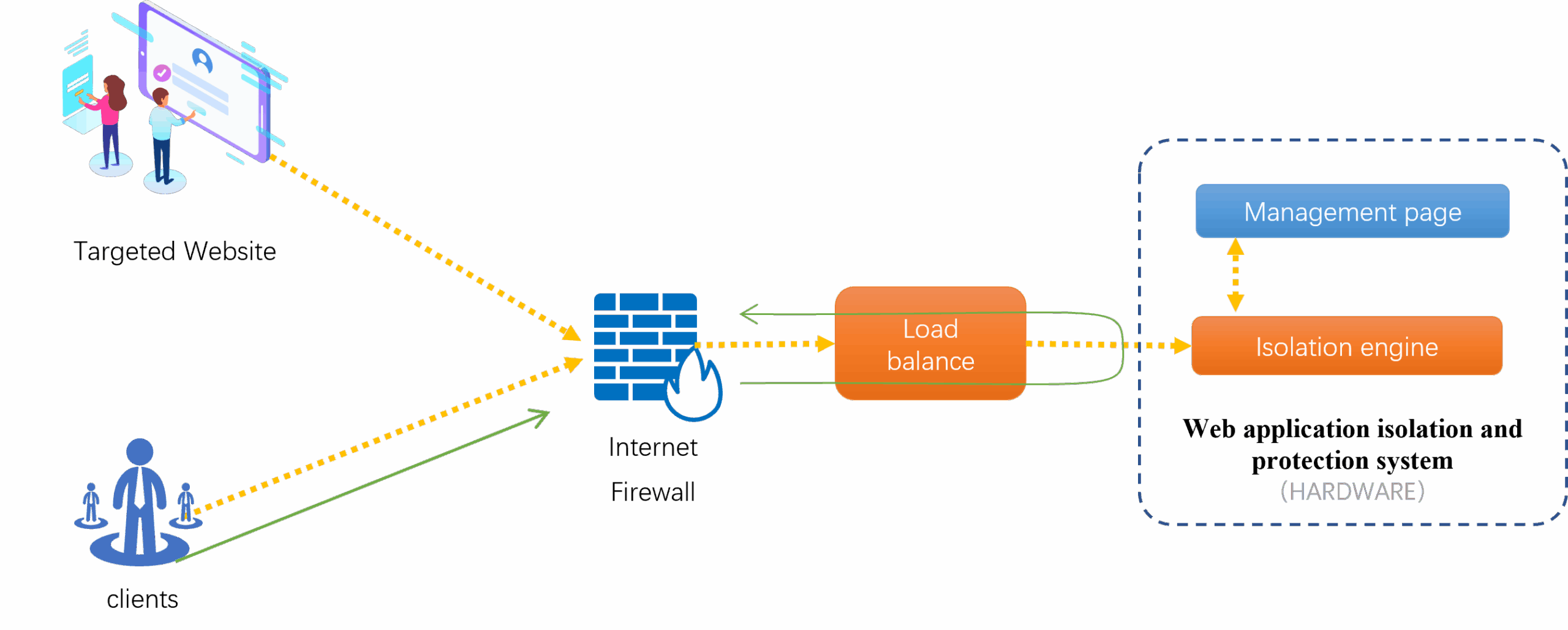
Typical Deployment
The product is offered in both software and hardware forms, and requires users to provide the following information:
- Origin IP Configuration: Configure load balancing to handle origin IPs (e.g., preserve client IP for backend servers).
- Two IP addresses required.
- DNS Resolution: Provide DNS server addresses for domain name resolution.