Product Overview
Signature verification server can provide digital signature services based on digital certificates for all kinds of electronic information data, electronic documents, etc., and can verify the authenticity and validity of the signature data; support for user certificate verification of different CA’s, and provide a variety of ways to verify the validity of certificates based on the root CA/CRL/OCSP. To meet the needs of users in the network behavior of authenticity, non-repudiation, integrity, confidentiality and so on.
Provides enterprises and institutions with secure, efficient, and compliant digital signature and verification services, ensuring data integrity, authenticity, and non‑repudiation. Core functions include digital signing, signature verification, and certificate management.
Key Features & Functions
System Security
Uses transparent encryption technology to implement encryption without modifying applications or business structures.
High Reliability
Secure access control mechanisms; supports active–active deployment, cold‑standby, and recovery to ensure high availability and disaster recovery for cryptographic operations.
Key Security
Employs a three‑tier key protection structure (“System Master Key – User Key – Session Key”) to ensure critical keys never appear in plaintext outside the device. Backup key files are protected by encryption.
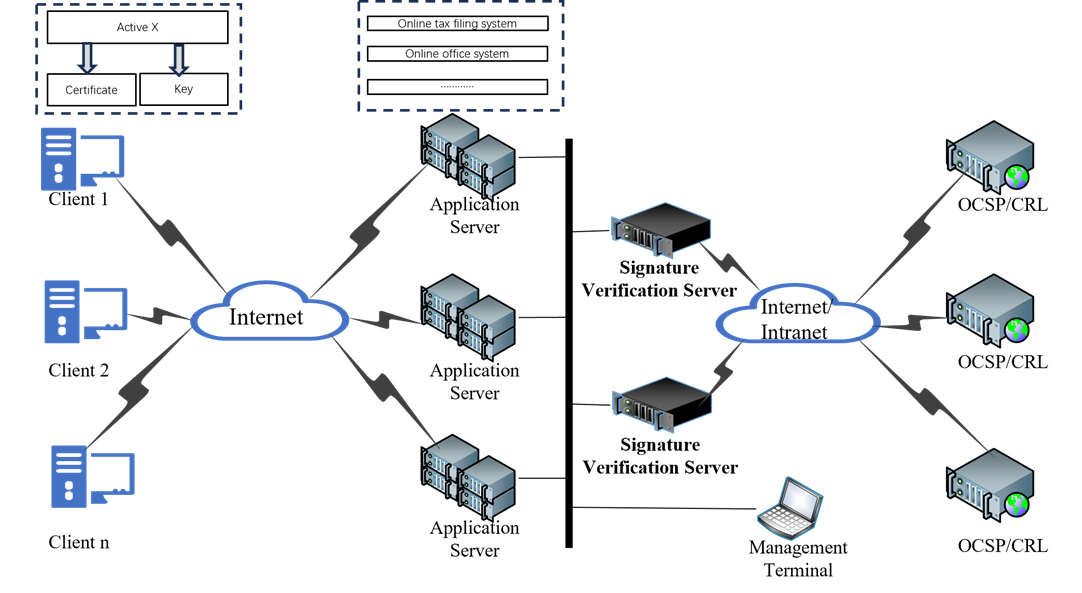
TYPICAL APPLICATION
The signature verification server can be widely used in systems such as e-government, e-commerce, and online office applications. For example, it can be applied in online declaration and approval for government agencies, online tax filing, online banking, online securities trading, and online shopping in e-commerce; in office systems such as OA, finance, and human resources. The signature verification server provides digital certificate-based signing/verification, certificate validity validation, data confidentiality protection, and more in these systems, meeting the user’s needs for non-repudiation, information integrity, and confidentiality in online activities.