Product Overview
Cryptographic Server is a high-performance cryptographic equipment, can be applied to various types of cryptographic security application systems, high-speed, multi-tasking parallel processing of cryptographic operations, to meet the application system data signature/verification, encryption/decryption requirements, to ensure the confidentiality, integrity and validity of the transmission of information at the same time to provide security, improve the key management mechanism, has been applied to the online examination and approval, office, online banking, online securities, online payment and other e-government, e-commerce and enterprise informatization systems, for the development of social information technology security. It has been applied in online approval, online office, online banking, online securities, online payment and other e-government, e-commerce and enterprise informatization systems, providing security for the development of social informatization.
Cryptographic machine as an important security equipment deployed in the application server side, the realization of key generation, management and high-speed signature, verification of signatures, data encryption, data decryption and other operations, identity authentication, transaction signature verification, data encryption and decryption and other aspects of the business has a strong supporting role, is the information security industry chain is the most basic, indispensable hardware cryptographic equipment.
Key Features & Functions
- Compatible with international algorithms RSA, ECDSA, DSA, 3DES, AES, HMAC, etc., with good scalability.
- Cryptograph API interface supports PKCS#11, JCE and other international standard interfaces with good versatility.
- Adopting the three-layer key protection structure of “system protection key – user key (internal key pair or KEK) – session key”, which fully guarantees the security of user key and application system.
- Ensure that the key does not appear in plaintext outside the device at any time, and the key backup file is also protected by the encryption of the master key.
- With the support of connection password and whitelist, it realizes the authorization and authentication of the cryptograph to the application server, which further improves the security of the system. Multi-computer parallelism can provide fault-tolerance, so that business operations are not affected when a cryptographic machine fails. Multi-computer parallelism can also improve the performance of cryptographic operations.
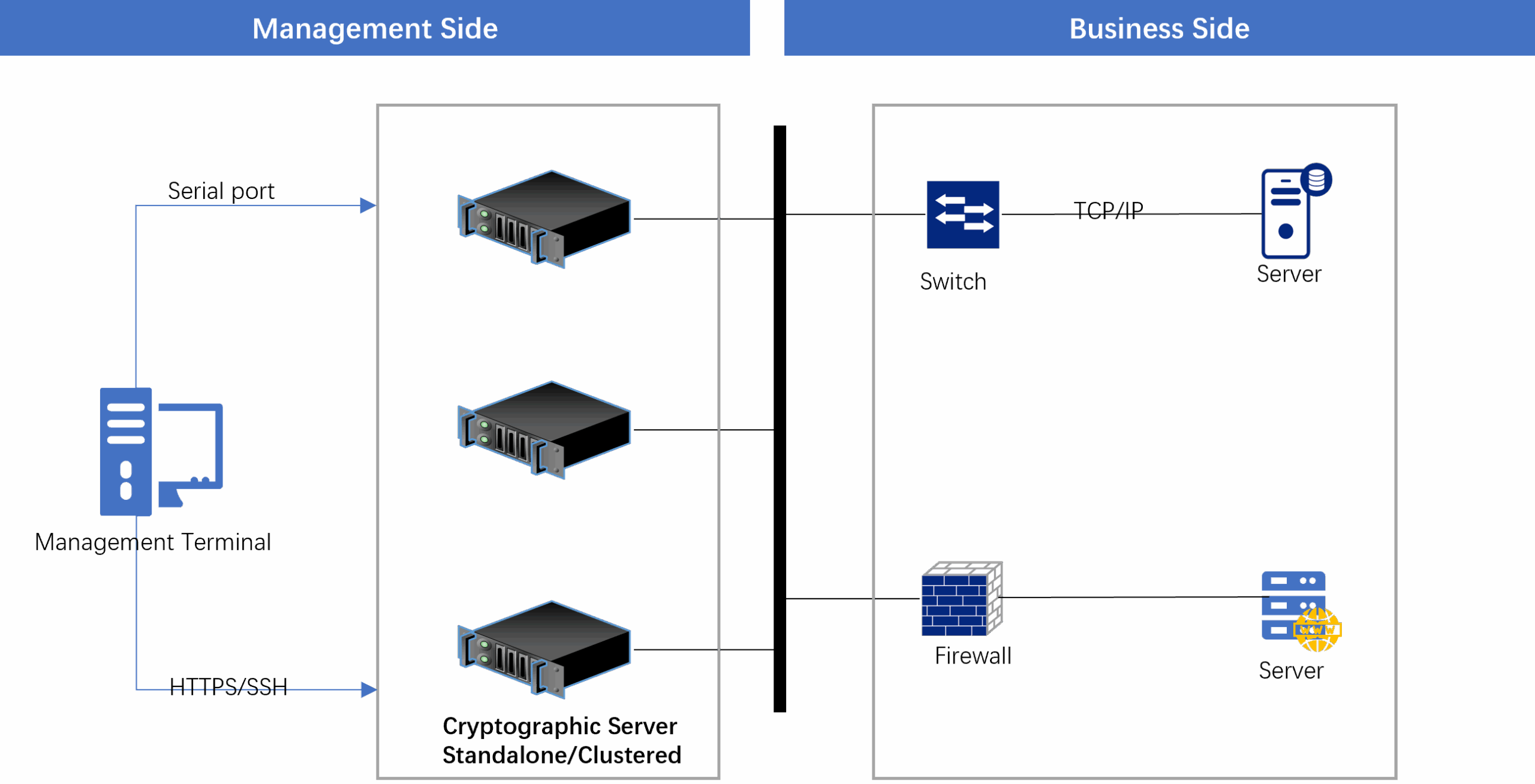
TypicalDeployment
The cryptographic server supports both standalone and clustered deployments. Clustered deployment enhances cryptographic performance and device redundancy. In the event of a failure in one of the servers within the cluster, the business system can continue to operate without interruption.